An online, managed or remote backup service supplies users having a system for storing and backing up their PC files. On the internet backup issuers are business enterprises that provide this type of service to customers over the Internet. These over the internet methods generally run on a schedule, sometimes once a day during the night whilst computer systems won't be being used. Commonly constructed around a client software program, these backup services compress, collect, encrypt and transport the info to the remote backup service provider's servers or off-site hardware.
Cloud Enablement Solutions
Do you even know how many illustrations you've on your hard drive? Are they all saved in 1 place or unfold throughout a variety computers and memory cards and public websites? An incredible number of hard drives crash every year (statistically, around 6%) and all of their records are lost. Most of us have several gigabytes of photographs and, if you're smart, you'll have a backup copy of all of these photos. A impressive answer for covering your thoughts is a web remote backup service along the lines of mozy, elephant drive, or myotherdrive. But in advance of you go with a backup service, you'll find a few belongings you ought to know.
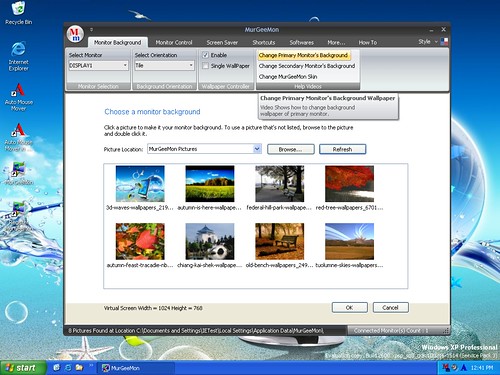
Remote backup services function spontaneously to outlet information on a routine, timed for basis, creating extensive data images. Notifications are immediately generated for failed backup periods to attract interest from help staff. Late graphics are saved on disk for instant retrieval, and long-term archival data is routed via a solitary entry point, guaranteeing that data can be discovered whenever it's needed.
Remote backup service providers remove the need for capital outlays and bodily space. Information backup routines automate the backup system as a way to lower operating costs and eradicate overhead in the form of support personnel and equipment servicing and upgrades.
With technology advancing on the beat with which it offers over the last decade, remote monitoring and remote control controlling of infrastructure has become more streamlined and much more reliable. With all the advent of higher speeds throughout the internet, a greater number of CTO's are confident with offshoring infrastructure operations to an skilled vendor, who won't essentially might want to be positioned in the same city. With most vendors themselves creating redundant hyperlinks to some other customer's network, CTO's can easily sleep more advantageous knowing that their infrastructure is in safer hands.
Console: Avocent’s Cyclades ACS console servers are available in single and twin strength provide options. Whenever combined with built-in power administration and centralized administration, these gadgets make available secure and consolidated out-of-band infrastructure management. ACS console servers utilize a Linux working system, are accessible both in-band and out-of-band, and now have detailed logging capabilities and various safety features.
Data Flexibility
Mission critical data, whether it really is ten days or 10 yrs. old, requires a too high diploma of accessibility in order to offer the necessary flexibility to satisfy company opportunities. Remote backup services are accessed via only one point via a net connection. Instead of having to hunt down tapes, the data is prepared for any end utilizer to quickly retrieve. Having information obtainable at one's fingertips will allow for each staff member to focus their attention on their aims rather than technological know-how or having to demand IT support.
Lots more revealed about remote management service here.
Li Braymiller is this weeks Remote Management Service savant who also reveals strategies download simulation games,uss monitor crew,cute usb hub on their web resource.